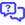Password Rotation
The Password Rotation feature matches and updates all the passwords including user, any kind of administrator, and global administrator passwords in any of the following sources:
- On-premise Active Directory
- Microsoft Entra ID
- Microsoft 365
NOTE If you experience issues adding Global Administrator or User Administrator roles to Microsoft tenants and don't have Microsoft P1/P2 licenses, proceed to this link to add those roles with the PowerShell module for free.
Password Rotation organizes the records based on criteria such as a username and domain, and rotates passwords when a match is found. After rotation, the newly generated passwords will be updated in the Microsoft Entra ID, on-premise Active Directory, Microsoft 365, and IT Glue.
The Network Glue collector needs a domain administrator account to rotate Active Directory passwords. If your Network Glue collector uses the local system account, you will receive "The server cannot handle directory requests" error when attempting to rotate a password.
IMPORTANT Write permissions are also required to rotate passwords.
Personal passwords can be rotated.
Prerequisites
For on-premises Active Directory password rotation
- An active Network Glue setup.
- Scan Active Directory must be turned on.
- Administrator access to IT Glue. The feature is available for custom roles with administrator rights.
NOTE Active Directory settings should be filled out. For more information, see Setting up Network Glue for an IT Glue organization.
IMPORTANT In environments using work groups, user and password information is collected directly from the windows machines and not the domain controller. As a result, the Network Glue collector sends requests to each individual machine. If a machine is off for more than a 10-day period, an Active Directory password rotation may fail for a user.
Enabling Scan Active Directory
Turn on the Scan Active Directory toggle on the Network Glue > [network name] > Edit Network page and click Save.
ALERT The AD password must be updated to ensure sync can continue with Network Glue.
Admin passwords that are used to set up the Active Directory connection with Network Glue, can be rotated. To rotate this password, users need to match network to a corresponding password in the Network Settings/account/networks. Until the user matches the corresponding Admin password in the settings, they will get the "Not Permitted" status when trying to rotate it.
With the on-premises Active Directory password rotation feature, IT Glue administrators can rotate “Protected User” from a Windows AD environment in IT Glue.
For Microsoft Entra ID password rotation
- An active Network Glue setup.
- An active account in entra.microsoft.com to be able to generate Microsoft credentials in their Active Directory account for further integration with IT Glue.
- Sync data settings in the "Edit Credentials" of your Microsoft integration. For more information see, Microsoft Integration.
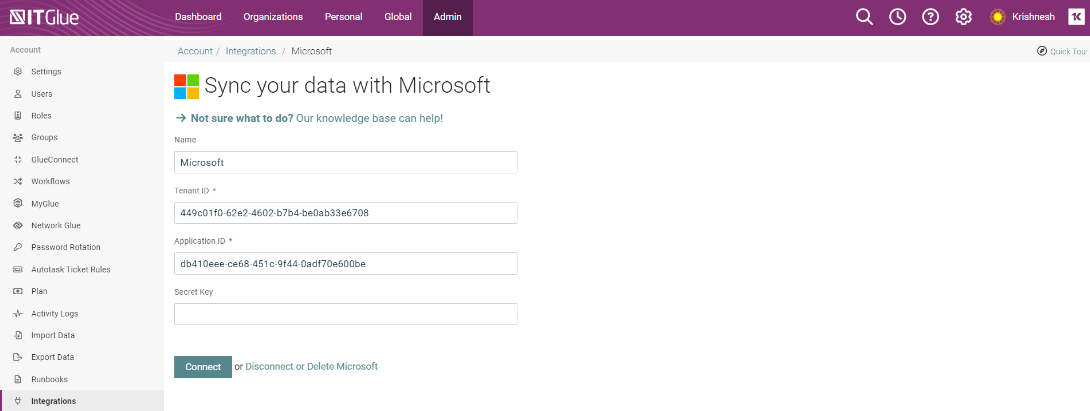
- If you have either new or an existing Microsoft integration, make sure that you have added required additional API Permissions when setting up Microsoft Integration on entra.microsoft.com.
To rotate passwords in the Microsoft Entra ID, you need to add the following permissions for the tenant.
- User.ManageIdentities.All
- User.EnableDisableAccount.All
- User.ReadWrite.All
- Directory.ReadWrite.All
- Directory.AccessAsUser.All
For more information, refer to Microsoft Integration.
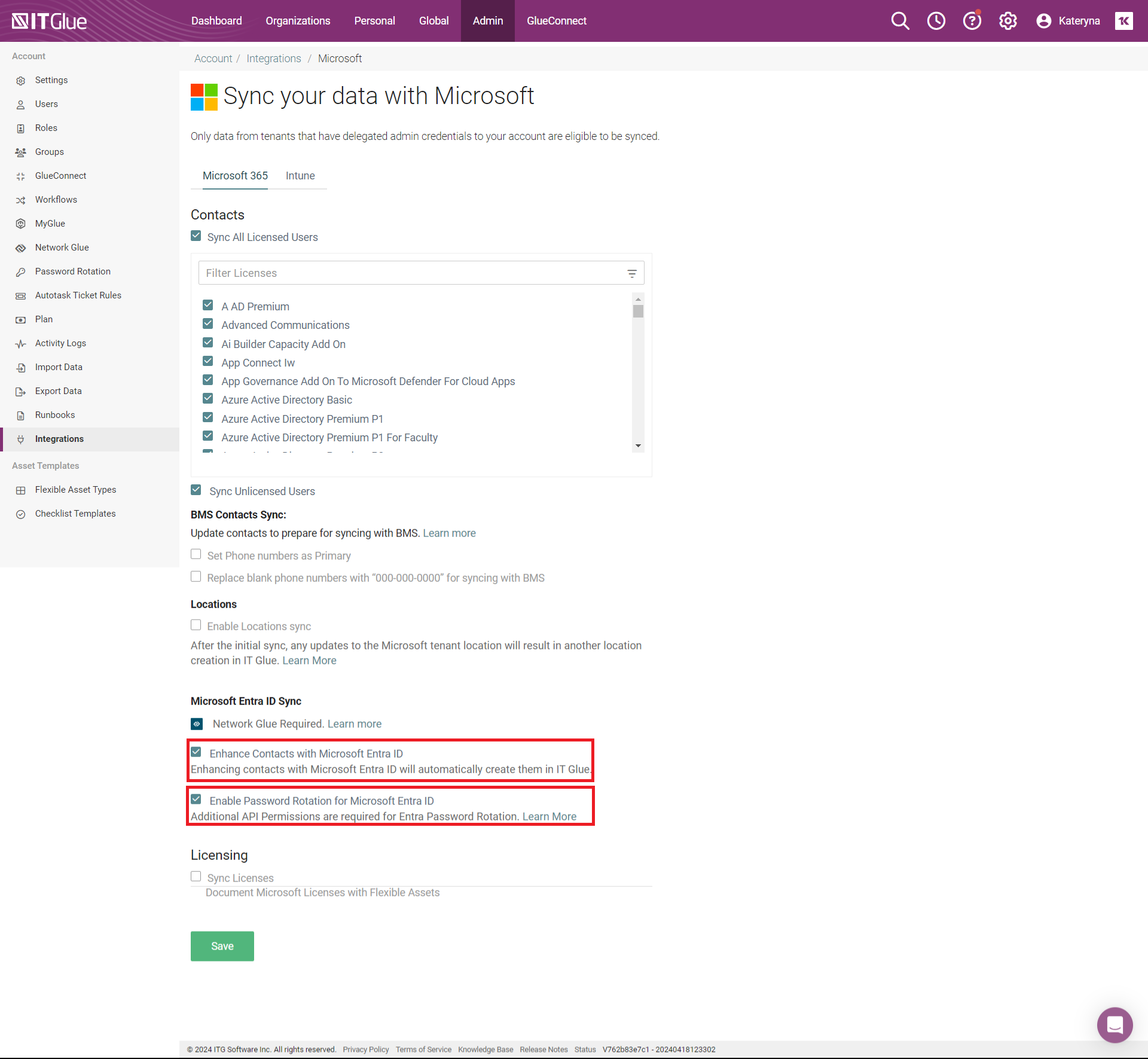
- Ensure that both settings are activated in the Microsoft Entra ID Sync section of your Microsoft Integration in IT Glue:
- Enhance Contacts with Microsoft Entra ID
- Enable Password Rotation for Microsoft Entra ID
For Microsoft Entra ID and on-premises Active Directory password rotation
If you have both on-premises Active Directory and Microsoft Entra ID and have a requirement to rotate passwords for both, you will have the settings enabled for on-premise Active Directory and for Microsoft Entra ID.
If you manage and store users both in Microsoft Entra ID and on-premise Active Directory and want to rotate passwords for them, please note that for users who have the same usernames it is required to have Entra Connect configured on your side in your Microsoft account.
Configuring Password Rotation
Complete the following steps in IT Glue to enable the Password Rotation feature:
- From the top navigation menu, click Admin.
- From the left navigation menu, click Password Rotation.
- Turn on the Enable Password Rotation toggle.
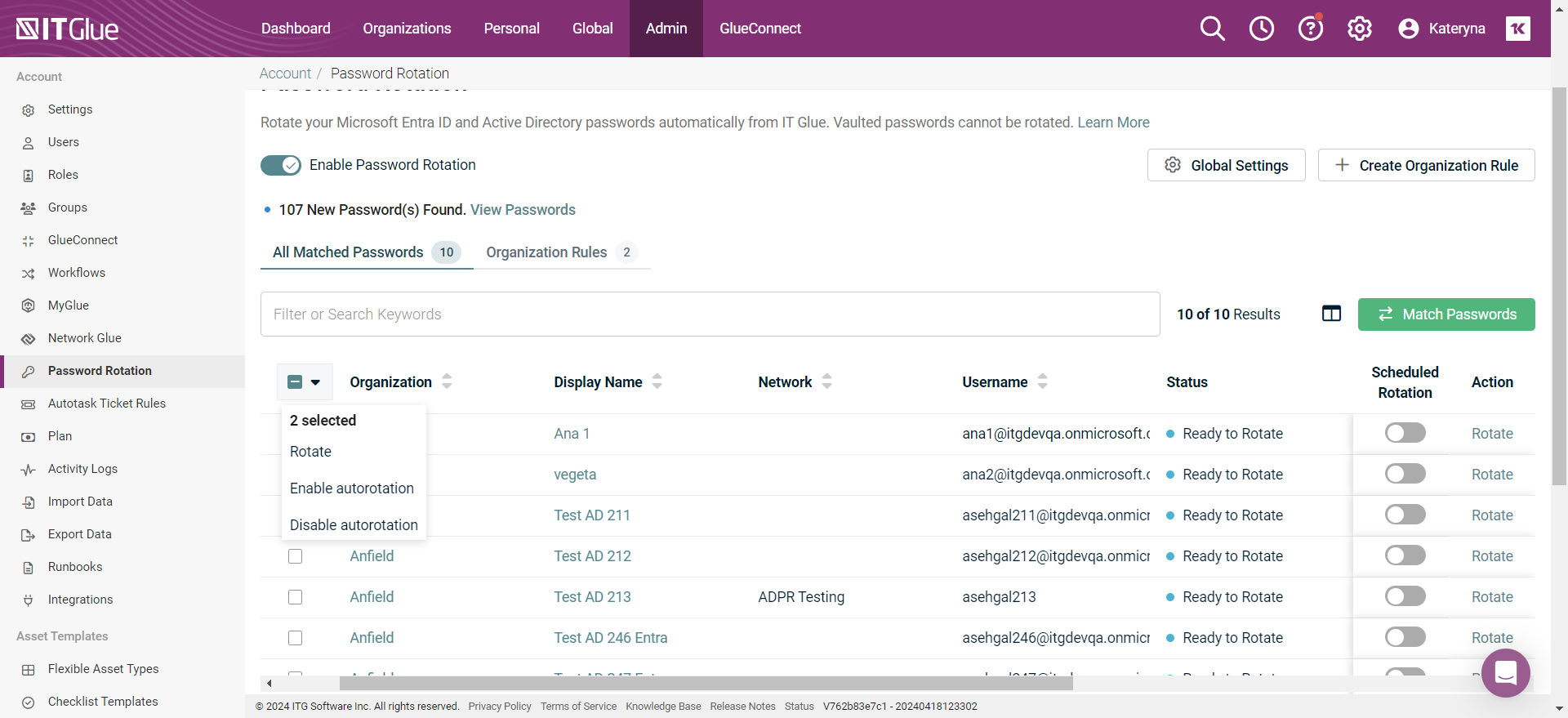
NOTE The Enable Password Rotation toggle activates both on-premises Active Directory and Microsoft Entra ID password rotation.
Configuring settings
In the upper-right corner of the page, click Global Settings to define global settings for the password policy or Create Organization Rule to configure separate password rotation rules for different organizations and override global settings. The created organization rule will be applied to all the individual passwords inside the specific organization.
Password Complexity
From the drop-down menu, select one of the following options:
- Complex Password: Enter the minimum character length of a password and select the character requirements for a password.
- Passphrase Password: When selected, a generated password will consist of six randomly generated words and will have at least one uppercase letter, one lowercase letter, one digit, and one symbol to meet your on-premises Active Directory and Entra ID password policies after a successful password rotation.
NOTE If any of the check boxes are not selected, the password rotation will occur according to the basic password policy.
NOTE Complex passwords are selected by default for global settings and organization rule settings. Organization rule settings override global settings.
Scheduled Rotation
Turn on the Enable Scheduled Rotation toggle to to select the frequency at which to rotate your matched password. For more information, refer to Password Rotation Scheduler.
Reviewing organization rules
Any configured organization rules are listed in the Organization Rules tab on the Password Rotation page. To edit or delete an organization rule, click the respective icons in the Actions column.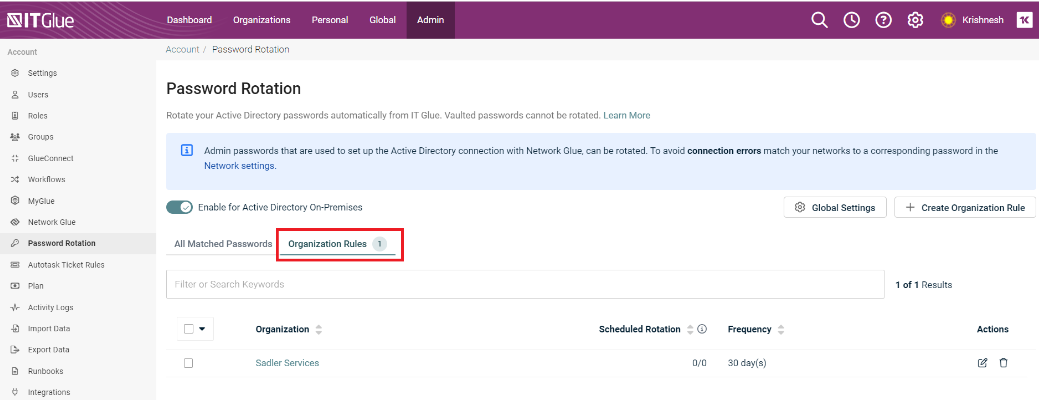
NOTE If you delete an organization rule, the global settings rules are applied to the passwords belonging to that organization.
NOTE To receive email notification when passwords are rotated for specific organization in terms of the set organization rule, navigate to My Settings from the drop-down menu and select the option Active Directory Password Rotation by Organization Rule in the Email Notification section. You will stop receiving notification if you disable this option.
Matching passwords
- Click Match Passwords to filter and approve the password matches.
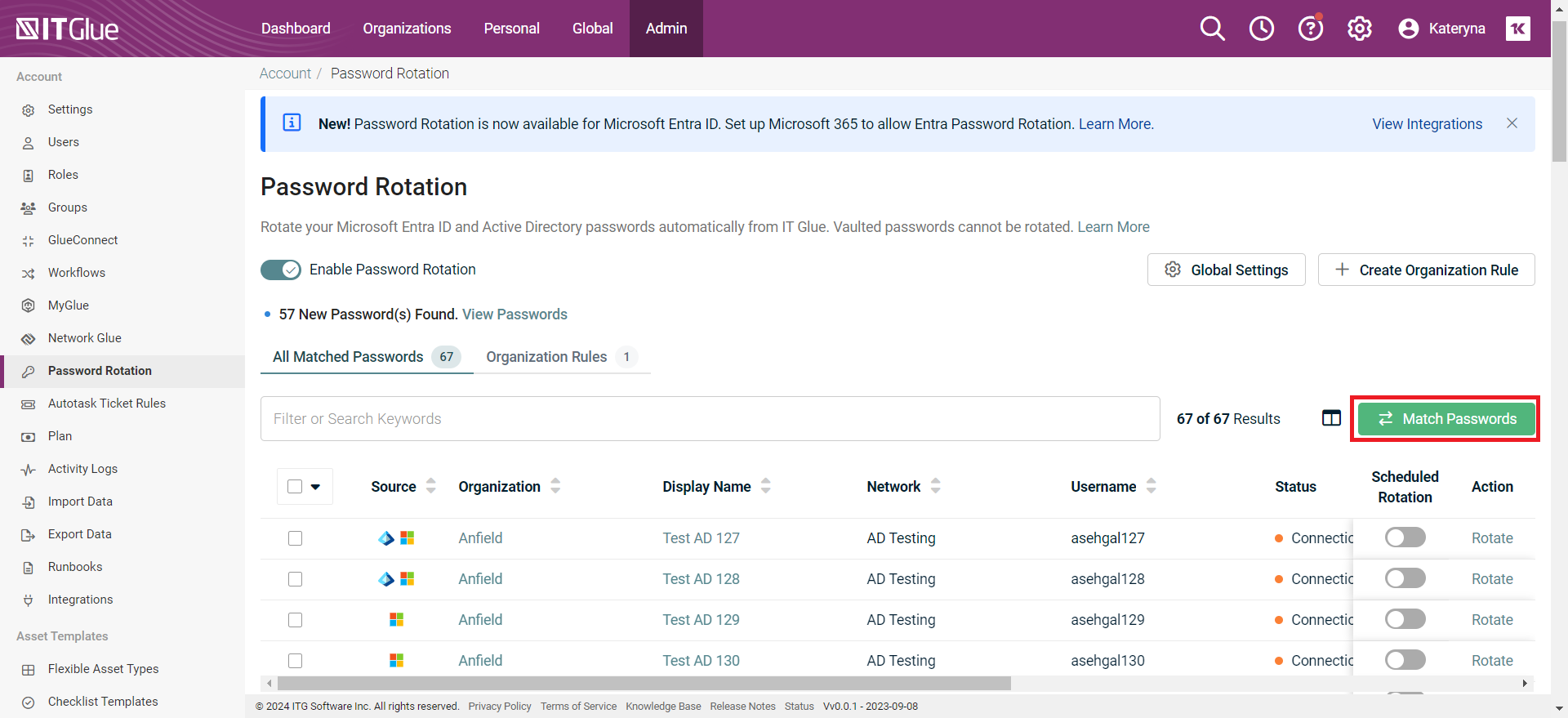
- Matching passwords on this tab will not change password in Active Directory.
- Matching is required to ensure that the password rotation is correctly applied between your users in Active Directory and IT Glue.
- After the rotation is performed, the newly created password will match between IT Glue and Active Directory.
- If you change passwords manually in IT Glue, the change will not return to Active Directory directly unless you click rotate and the rotation is successful.
- Confirming matched passwords also serves as your approval for IT Glue to rotate a password.
- IT Glue will present your password from Active Directory and suggest matches for you. In the Unmatched tab in the Match Passwords window, select the preset filter Suggested to sort the list by suggested matches.
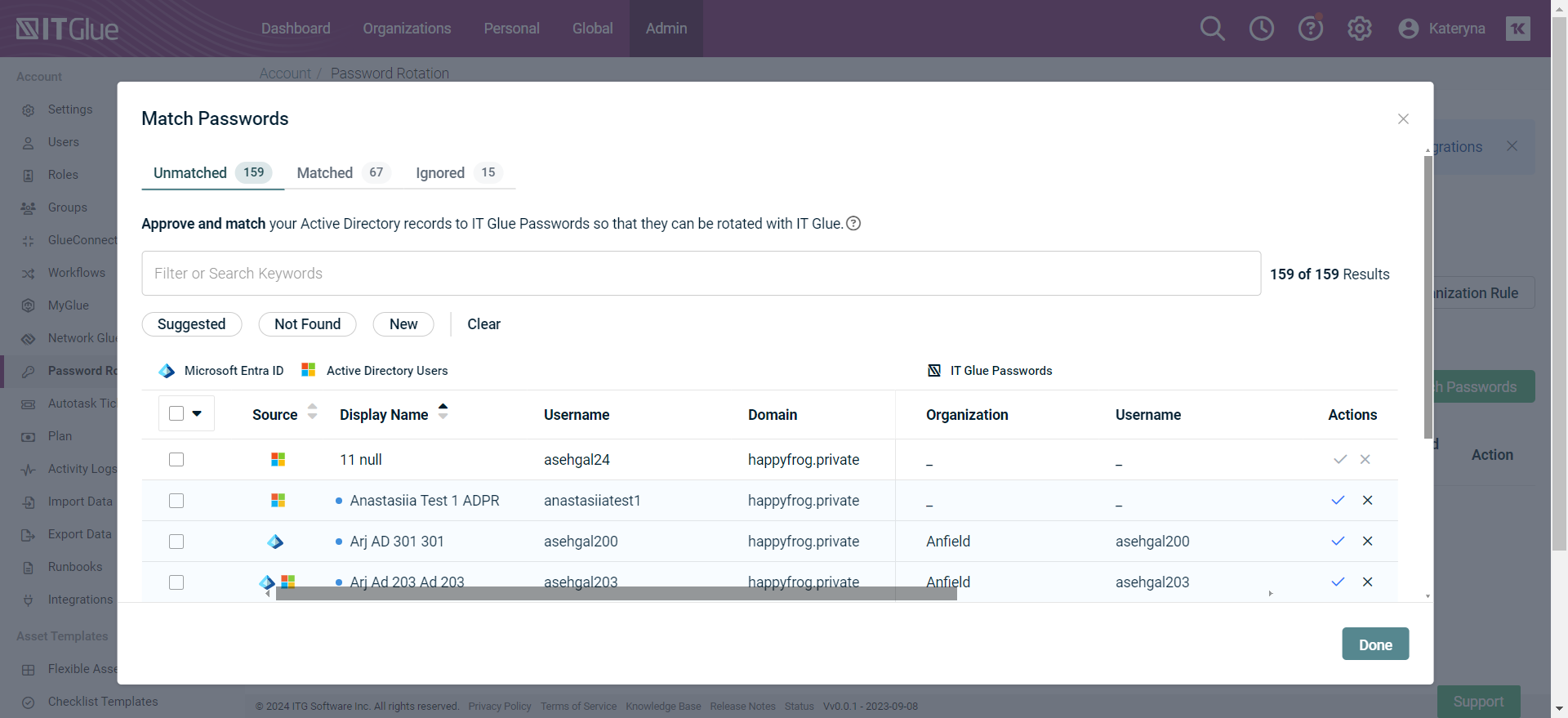
NOTE You are not able to match multiple contacts to the same password. If that password is deleted, it will cause an error.
- Suggested matches are based on exact username.
- A green check mark will appear under Actions when an individual match is found.
- A gray check mark will appear when no match or multiple matches are found. You must then search and select a password.
- The X option will move the password to the Ignored tab.
- For bulk matching, select the check box for the password records you want to match and click Approve or Ignore. The approved records will be displayed in the Matched tab.
- Click the value and select the correct name from the drop-down list as shown in the screenshot below.
- Click Done to when finished.
- The Ignored tab will contain passwords not approved for rotation, which will not count as unmatched items in subsequent syncs. To be able to rotate them again, click Match for single or multiple user passwords.
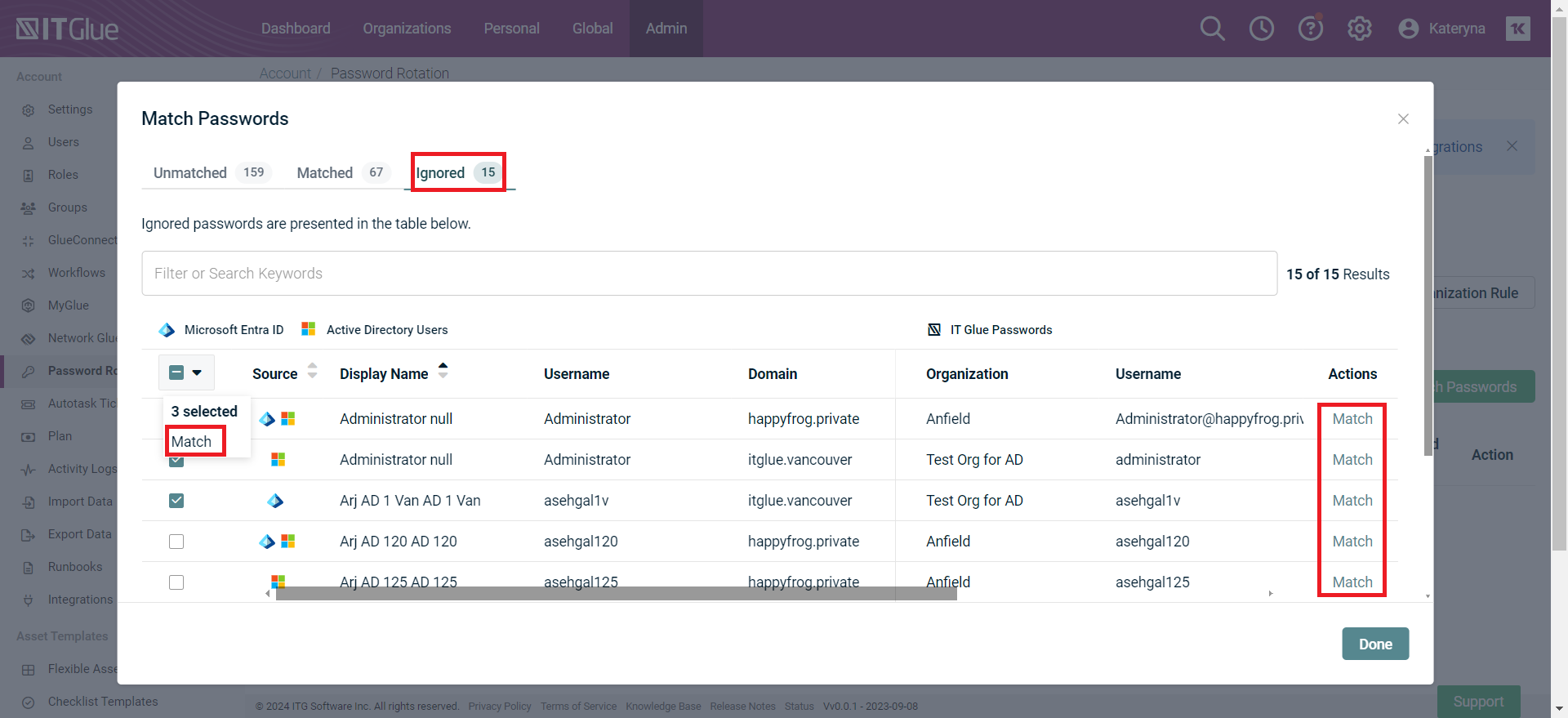
- Click Done. You can view the password-matched status on the Password Rotation page. To rotate a password, click Rotate in the Actions column.
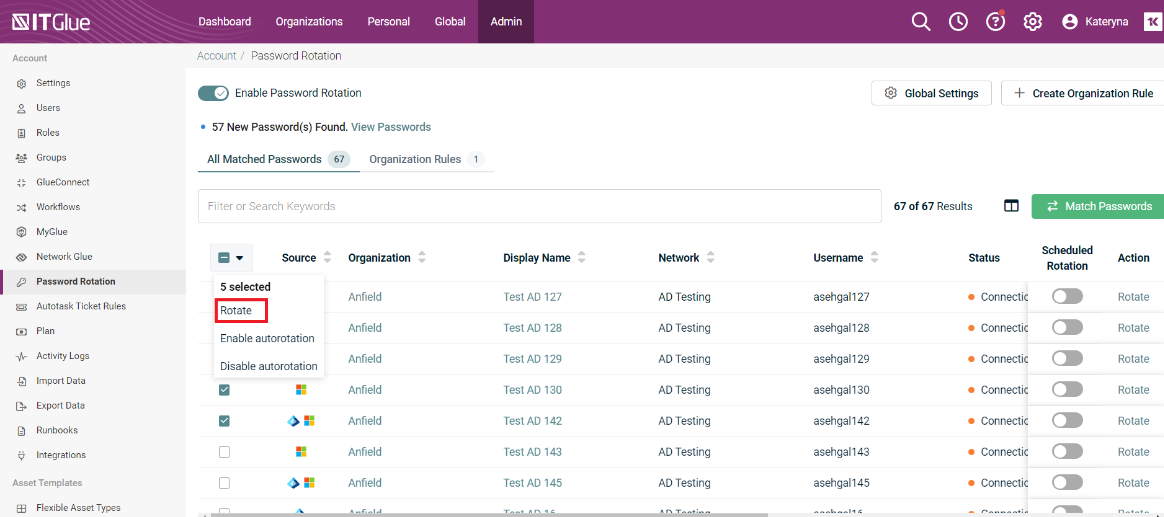
To rotate passwords in bulk, select multiple password check boxes and click Rotate.
You can also view the auto-rotation status by navigating to the organization to which the password belongs. To rotate a password from the Passwords page, click Rotate.
For an unwanted password match, click Ignore. These passwords will be displayed in the Ignored tab.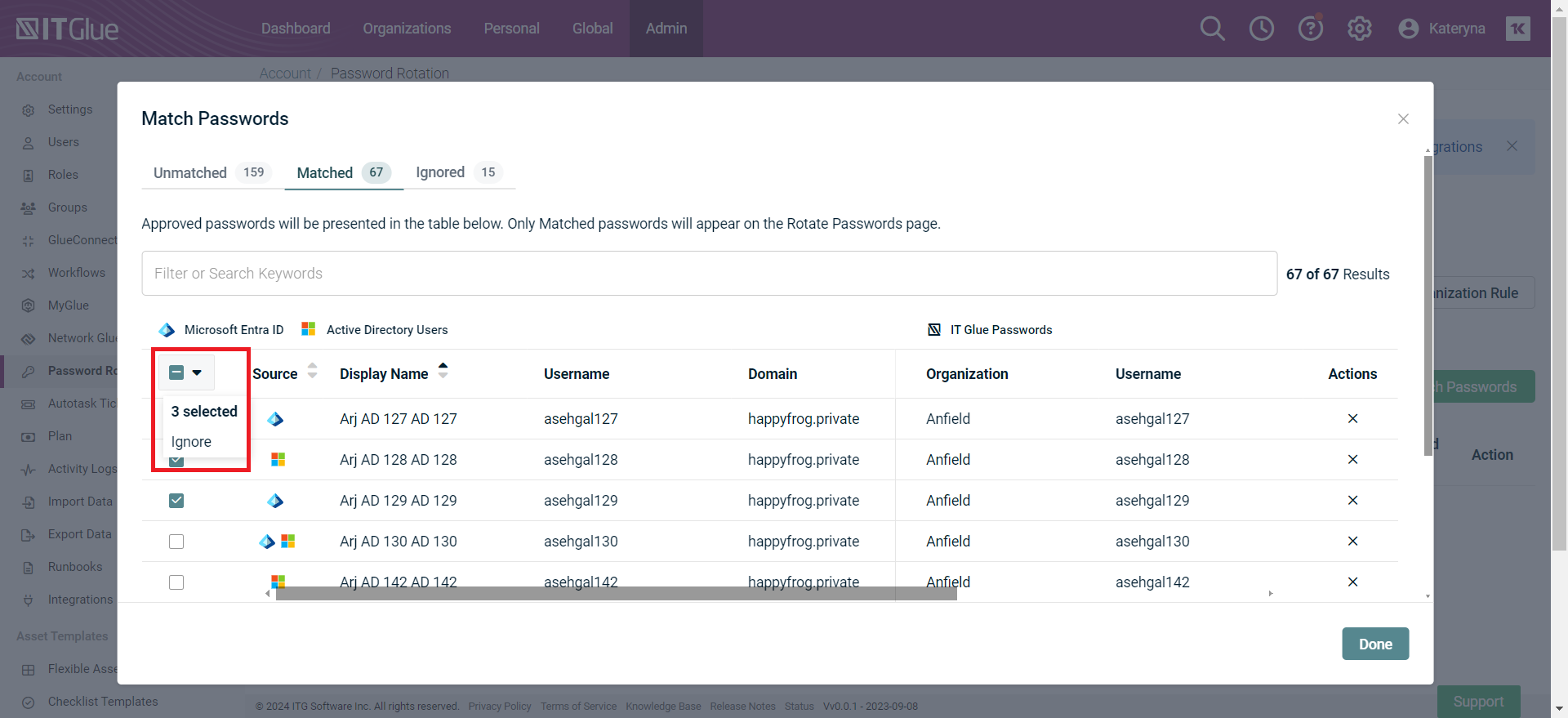
On the Matched page, you will see user passwords that are approved for rotation.
If a password was approved by mistake, click X or Ignore. The password will be moved back to the unmatched or Ignored tab.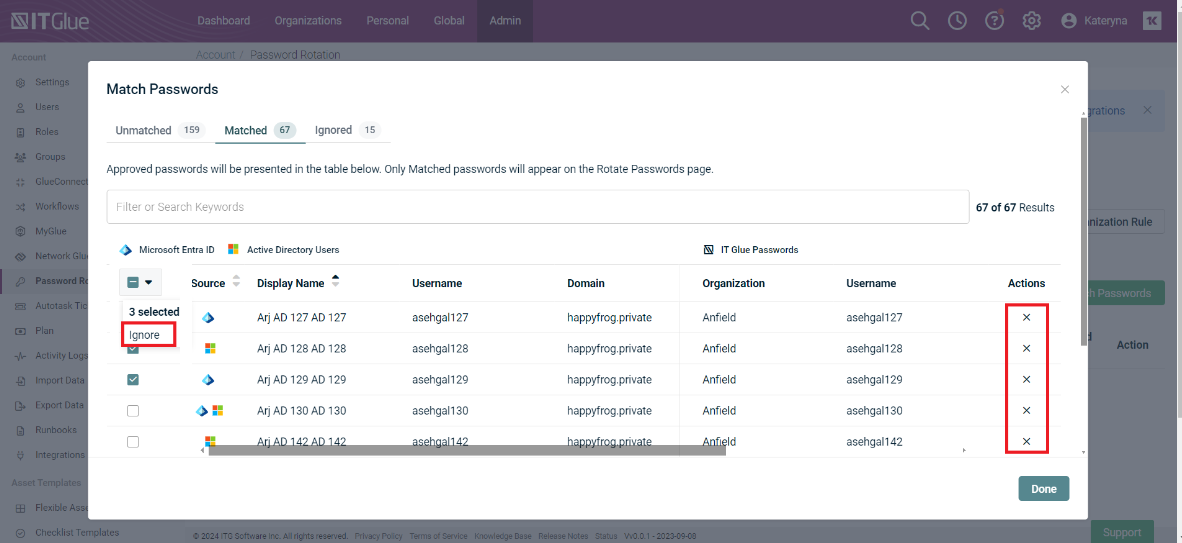
You can edit the suggested Password Name value if the suggested match is incorrect.
NOTE When a password is rotated by a user, the Revisions to core and flexible assets on the right sidebar will display a new version. By restoring to a previous version, the change will not be automatically updated in the Active Directory.
Using Cooper Bots to rotate Active Directory passwords in IT Glue
Cooper Bots is a Business Process Automation (BPA) Engine that combines the power of workflow automation with an AI assistant to execute work on a customer's behalf across the Kaseya platform. With Cooper Bots, you can set up a rule that will automatically rotate Active Directory passwords in IT Glue whenever a corresponding ticket is created in Autotask. Learn more about Cooper Bots in the KaseyaOne Help system.
NOTE Presently, Cooper Bots cannot rotate Microsoft Entra ID passwords.
BEFORE YOU BEGIN
• The Enable Contacts sync check box must be selected in the Autotask integration sync settings in IT Glue. Refer to Configure Autotask sync settings in IT Glue. IT Glue uses the contact to identify the password to rotate, so you must select this check box and select a contact when creating the Autotask ticket.
• The contacts synced from Autotask must match with remote contacts with rotatable passwords.
• The Active Directory toggle must be turned on in Network Glue.
In KaseyaOne, when creating the Cooper Bot, you'll configure the following settings to achieve this workflow:
- Select Autotask: Ticket Created as the trigger.
- Configure applicable conditions.
- Select password rotation as the action.
EXAMPLE If the ticket description contains the keywords forgot password, password rotation is triggered.
When the Cooper Bot is active, it will automatically identify Autotask tickets that request a password reset, this password will be found and rotated in Network Glue, and Cooper Bots will update the ticket with a link to the password that was reset for the technician to action.
Statuses and error messages
The following are the possible statuses shown after initiating a password rotation:
- API Error: An error happened prior the password rotation.
- Admin Not Permitted: Arequired admin role is not added for admin password rotation. Network Glue Admin Passwords cannot be rotated in bulk. You can still rotate individual Network Glue admin passwords. Additional API Permissions are Required for Microsoft Entra ID Password Rotation.
- Not Permitted Admin: You may receive this error in the following three scenarios:
- When the Network Glue Admin passwords cannot be rotated in bulk.
- When Network Glue Admin Entra ID passwords cannot be rotated in bulk.
- When additional API Permissions are required for Microsoft Entra ID Password Rotation.
- Multi Tenant not Permitted: The required role is not added for password rotation. You may receive this error in the following three scenarios:
- App has been removed from the all admin roles for side tenant.
- App has been removed from Global Admin and User Admin roles for the main tenant.
- The key API permission is turned off for the side tenant app in Microsoft.
- Not Permitted: Vaulted passwords are not permitted for password rotation.
- Successful: The passwords have been successfully rotated.
- In progress: The password rotation is in progress.
- Failed: The password rotation has failed.
NOTE If a user set up a minimum password age in the on-premise Active Directory and/or Microsoft Entra ID, and rotates the password in IT Glue, the next successful attempt to rotate this same password will accrue only after the completion of the period that is set up as the minimum password age.
The server cannot handle errors related to LDAP over SSL (LDAPS) connectivity issues. The following are the tips given below to troubleshoot these issues.
- Verify that the LDAP server has a valid SSL certificate and port 636 (LDAP + SSL) is open on the web server.
- Access the Microsoft's official article to troubleshoot LDAP over SSL connection connection issues. This might help you in resolving the issues.