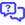Setting up single sign-on (SSO) to MyGlue
For partners subscribed to Basic with SSO 2021, Select with SSO 2021, and Enterprise plans.
Introduction
Single sign-on (SSO) provides an easy way to access multiple websites or applications using a single set of credentials. As the IT Glue Administrator or a Manager with access to all organizations, you can configure SSO for your clients using MyGlue so that they can sign in quickly, eliminate an extra set of credentials they have to remember, and streamline their overall working environment as they use SSO to access other sites and apps.
Prerequisites
- You must be an Administrator or a Manager with access to all organizations to configure SSO for MyGlue.
- Ensure the MyGlue client users are provisioned in a Security Assertion Markup Language (SAML 2.0) SSO identity provider with exactly the same email address as their MyGlue account. We don’t create user accounts under SSO.
- MyGlue users with iPhones must have iOS version 13.0 or above installed to use single sign-on (SSO) on the MyGlue mobile app. If they do not have version 13.0 or above installed, an error message “Single-Sign On (SSO) requires iOS version 13.0 and above. Please update your software in order to proceed” will appear. They will need to complete this action before they can sign in to the MyGlue mobile app.
NOTE The following steps apply only to Azure (Entra/Microsoft) SSO. For instructions on configuring other SSO providers, refer to the list directly before the Configuring your MyGlue account for SSO section.
Instructions
SSO Configuration for your MyGlue Client's Identity Provider
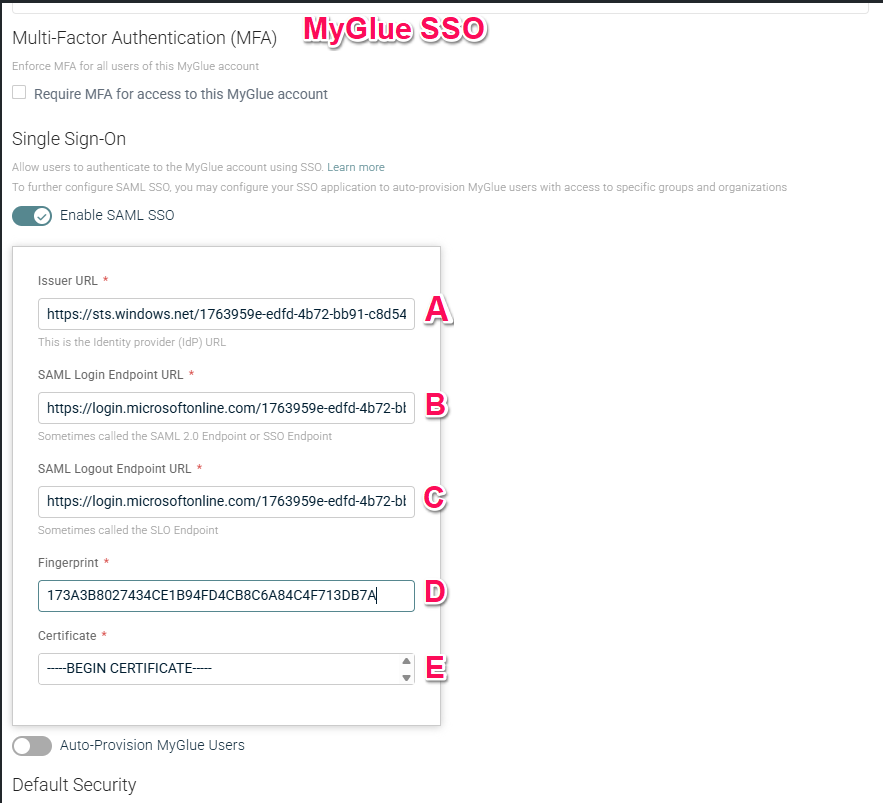
Regardless of which SAML 2.0 identity provider your client uses, you will need to enter the following URLs to configure your MyGlue client's identity provider for MyGlue SSO:
- Issuer URL - Microsoft Entra ID Identifier
- SAML Login Endpoint URL - Login URL
- SAML Logout Endpoint URL - Logout URL

To set up MyGlue SSO in your client's SSO portal, refer to the relevant KB article from the below list based on the SSO provider your MyGlue client is using.
NOTE The following articles refer to setting up SSO for IT Glue and the information entered into the fields that request your IT Glue subdomain and endpoint information should be replaced with the information in the image above with the blue number 4.
NOTE For EU partners, please use "https://app.eu.myglue.com" in all three fields above.
Configuring your MyGlue account for SSO
Now, you need to configure the MyGlue account to authenticate using SAML SSO. You will need a few pieces of information from your client’s identity provider to complete the steps.
- In IT Glue, navigate to Account > MyGlue > Edit Account.
- In the Single Sign-On section, turn the Enable SAML SSO toggle switch to ON. Once this is turned on, a form will appear. You will need to collect information from your client’s identity provider and enter it into this form.
- Issuer URL - The URL that uniquely identifies your SAML identity provider. Also called: Issuer, Identity Provider, Entity ID, IdP, IdP Metadata URL.
- SAML Login Endpoint URL - The SAML login endpoint URL of the SAML server. IT Glue redirects to this URL for SSO if a session isn't already established. Also called: Sign-on URL, Remote login URL, SSO URL, SSO Endpoint, SAML 2.0 URL, Identity Provider Sign-in URL, IdP Login URL, Single Sign-On Service URL.
- SAML Logout Endpoint URL - A URL where IT Glue can redirect users after they sign out of IT Glue. Also called: SLO Endpoint, SAML Logout URL, Trusted URL, Identity Provider Sign-out URL, Single Sign-Out Service URL.
Note: IT Glue does not support SSO logout URLs. - Fingerprint - The appropriate value based on the information provided by your identity provider. Also called: Thumbprint.
- Certificate - The authentication certificate issued by your identity provider (a base-64 encoded X.509 certificate). Be sure to include the entire certificate, including -----BEGIN CERTIFICATE----- and -----END CERTIFICATE------. Also called: Public Certificate, X.509 Certificate.
IMPORTANT Ensure there are no extra spaces trailing at the end of the Certificate string (i.e. after -----END CERTIFICATE-----).
- Click Save.
IMPORTANT Click Save only when all information has been entered. If you turn on SSO before the information is entered, it will break the sign in experience for all users on your account.
Setting up Just-in-Time (JIT) provisioning (optional)
MyGlue SSO supports JIT provisioning which allows MyGlue users to be automatically created when signing in via SAML SSO. New users will have access to MyGlue immediately without having to wait for an Administrator or Manager to set up their account.
- In IT Glue, navigate to Account > MyGlue. In the Actions drop-down, click Edit.
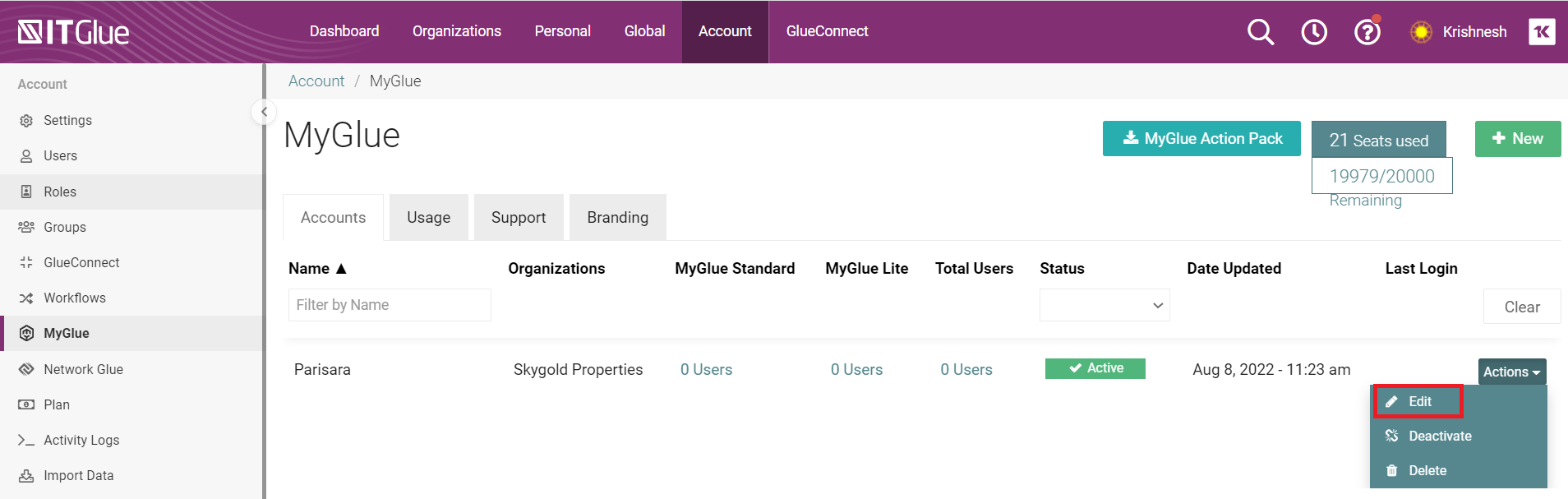
- In the Single Sign-On section, click to toggle the Auto-Provision MyGlue Users button to ON. Once this is turned on, a form will appear.
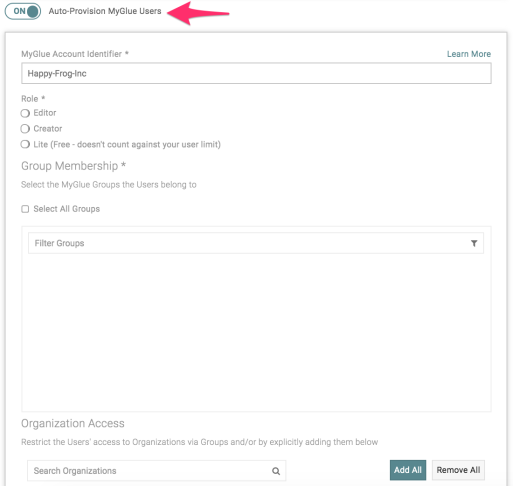
- Under the MyGlue Account Identifier heading, a default account name will auto-populate. You can edit this as needed.
IMPORTANT The MyGlue Account Identifier must be unique and communicated to your MyGlue users. They will need this account identifier to sign in successfully under JIT provisioning.
- Select a role (i.e. Editor, Creator, or Lite) to be assigned to all new users created through Just-in-Time provisioning.
- In the Group Membership section, select the groups that your new users will belong to. If desired, click the Select All Groups checkbox to select them all.
- In the Organization Access section, search for and select any organizations you want to restrict your new users from. If desired, click Allow All Organizations to select them all.
- Click Save.
NOTE Once you make all your changes, new MyGlue users will be able to use SSO to independently sign in and create new users directly via the MyGlue web app. Once created, users can sign-in using the MyGlue Chrome extension. When complete, test your MyGlue account to ensure the changes are applied correctly.
Testing MyGlue SSO Authentication
To make sure SSO is working for your MyGlue account, perform the below steps:
- Create a MyGlue user for yourself under this MyGlue account, or use an existing user if you have already created it.
- Sign out of and close MyGlue if you have a session open.
- In a new browser session, navigate directly to MyGlue.
- Enter your MyGlue email address and click Next.
- If you have set up JIT provisioning, enter your MyGlue Account Identifier.
You will be redirected to the identity provider you have just configured. Once credentials are entered into the SSO provider, you will be automatically redirected back to and signed into MyGlue.
Common Questions
How do we disable SSO for a user?
If a member has left your team, and you’d like to disable their user account, an Administrator or Manager will need to delete their account from the Account > Users page in IT Glue. We don't currently support disabling user accounts through the SSO server.
How can I set up SSO when creating a new MyGlue account?
You can enable SSO during new MyGlue account creation by following the steps in our Configuring and managing MyGlue accounts topic. In the Single Sign-On section of the setup, turn the Enable SAML SSO toggle switch to ON. Once this is turned on, a form will appear.
Then, complete the form by referring to step 2 from the Configuring your MyGlue Account section of this KB article.