Configuring single sign-on (SSO) with Azure
For partners subscribed to Basic with SSO 2021, Select with SSO 2021, and Enterprise plans.
This article explains how to configure the SAML SSO integration of the Microsoft Entra ID portal with IT Glue and MyGlue.
If you are configuring SSO for MyGlue using Azure, the instructions are the same but you will need to enter different values when configuring Azure and your MyGlue account settings page. Refer to Configuring SSO in MyGlue.
Prerequisites
- Microsoft Azure account with Microsoft Entra ID Premium activated.
- Administrator level access to IT Glue and a Global Admin or Co-admin account in Azure.
- All of your users under your account in IT Glue or MyGlue will need an account in Microsoft Entra ID with exactly the same email address. We don’t create user accounts under SSO.
- Before turning this feature on, log in to your IT Glue account twice: once in a regular browser and once in an incognito/private window. This is to ensure that you are still logged in to your account if you get locked out in the other window. Alternatively, you can also log in to two separate browsers.
Instructions
NOTE The steps below are required when setting up Azure SSO for IT Glue or My Glue.
- Log in to the Microsoft Azure portal.
- Navigate to Microsoft Entra ID.
- From the left navigation menu, navigate to Manage > Enterprise applications.
- Click New application.
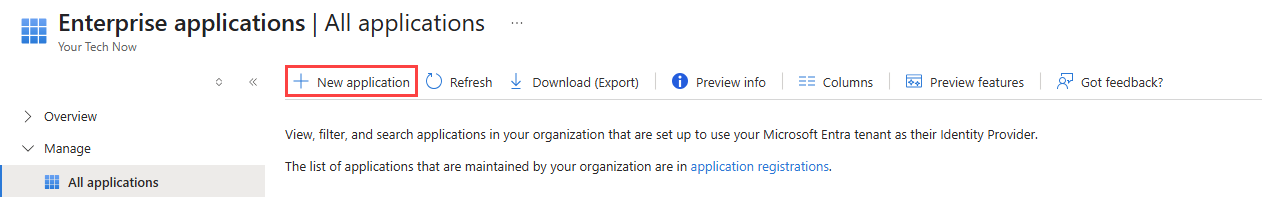
- Click Create your own application.
- Enter a name for the new application.
- Click Create to add the custom application to Microsoft Entra ID.
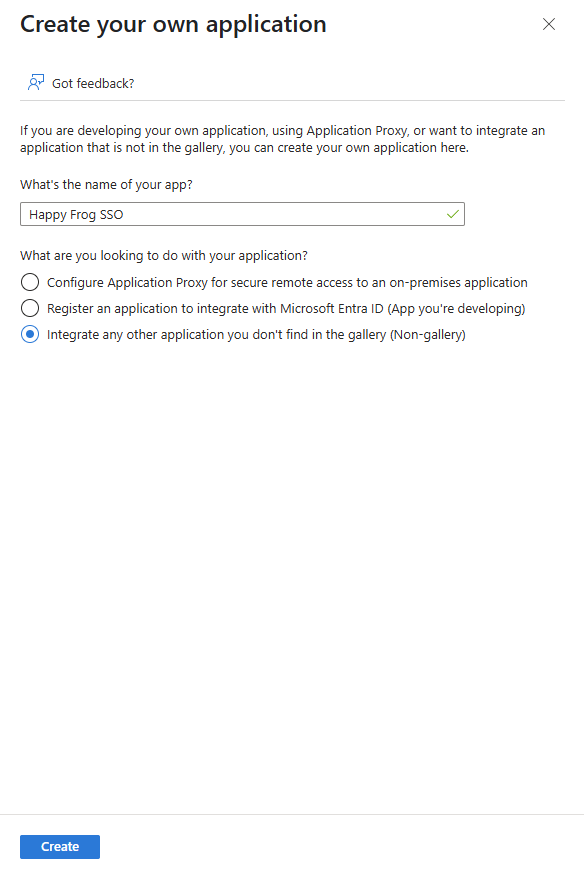
NOTE If you do not have Microsoft Entra ID Premium activated, you will not be able to enter the name of the application and an invite message to upgrade to Premium will appear.
- Once the application loads, click Assign users and groups.
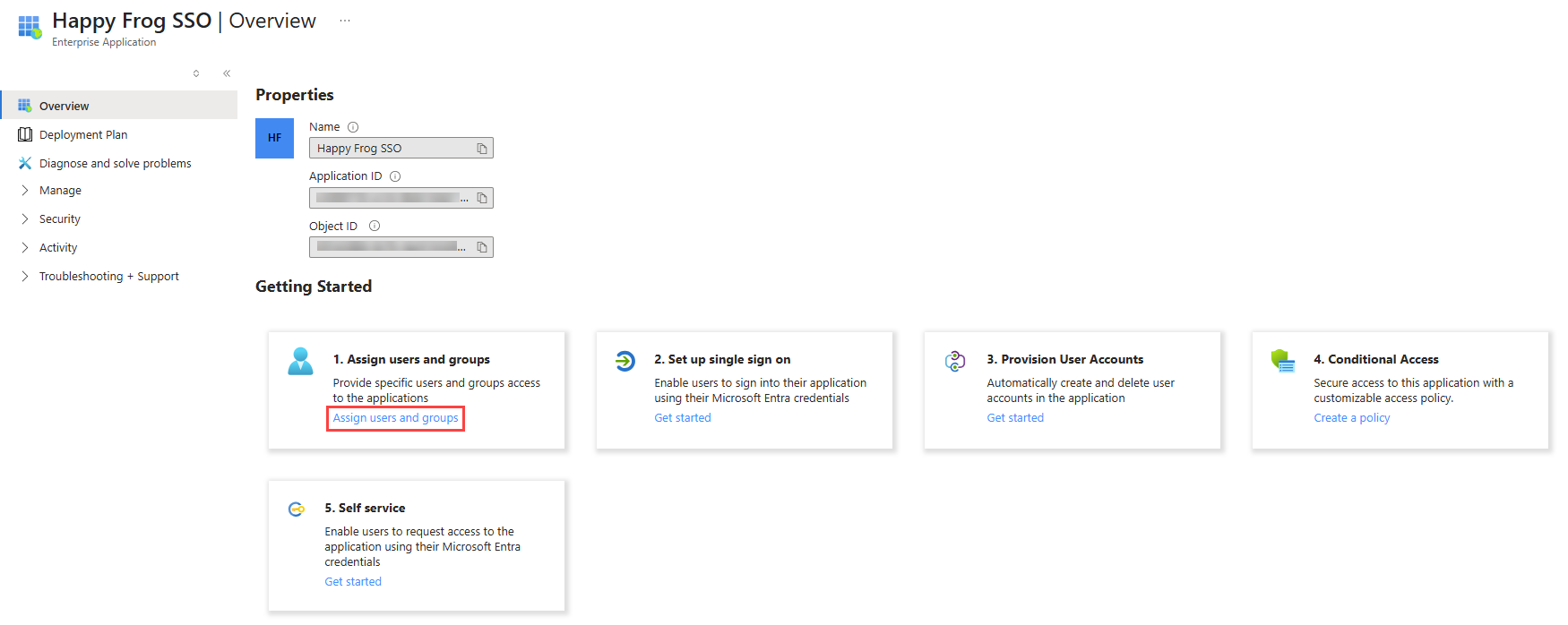
- Click Add user/group.
- Add users or user groups to this application as necessary, and click Assign.
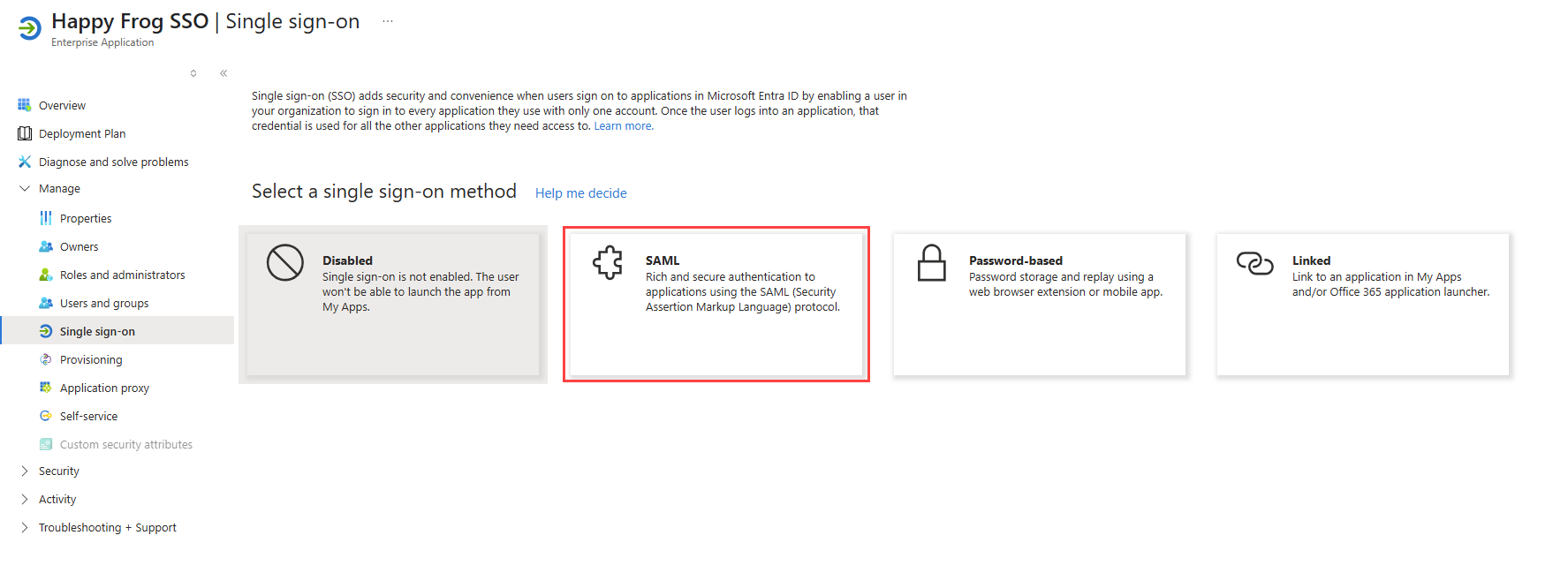
- Next, from the left navigation menu, click Single sign-on.
- Click the SAML tile.
Configuring Azure
Basic SAML Configuration for setting up IT Glue SSO
Follow the steps below to enable basic SAML configuration for IT Glue SSO.
IMPORTANT The SAML Basic Configuration needs to be set up separately for IT Glue and MyGlue because each platform requires different Login URLs to be entered during Azure configuration. Refer to Configuring SSO in IT Glue and Configuring SSO in MyGlue.
Attributes & Claims
- In the Attributes & Claims tile, click the Edit pencil icon.
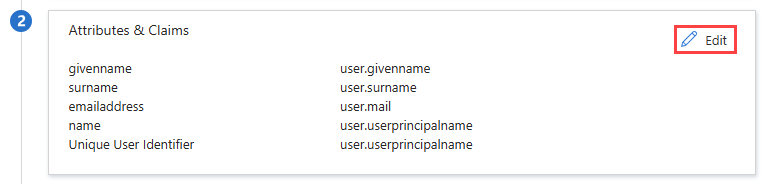
- Click Unique User Identifier (Name ID).
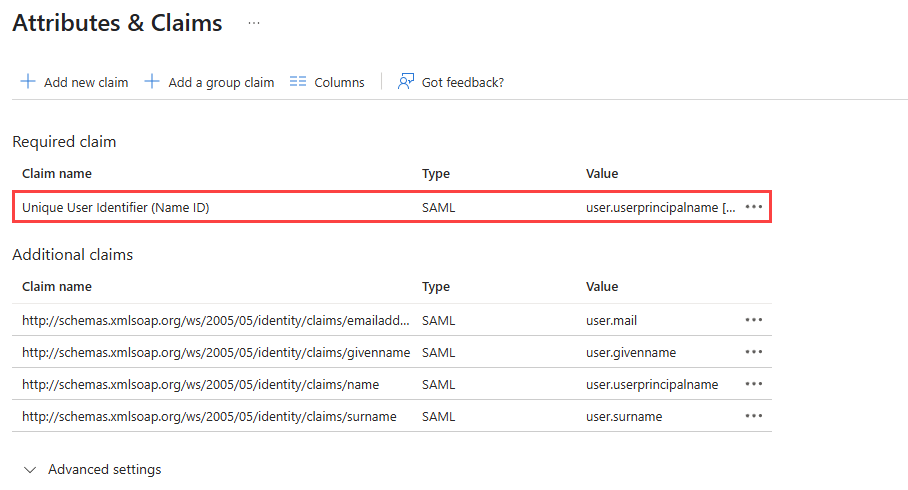
- Fill in the required fields.
- From the Source attribute drop-down menu, select user.mail.
- Click Save at the top of the page.
SAML Certificates
- In the SAML Certificates tile, click the Edit pencil icon.
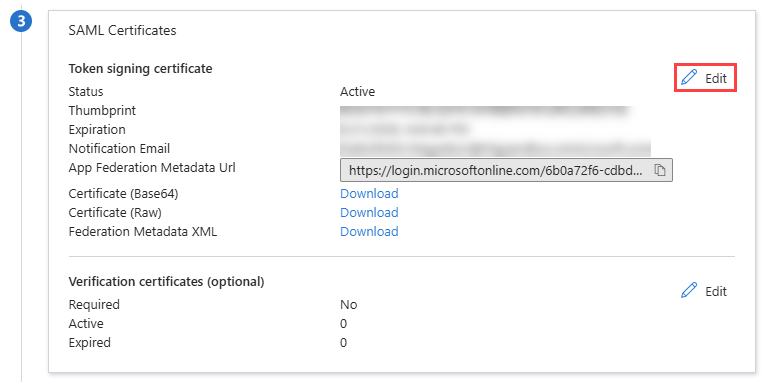
- In the Notification Email Addresses section, enter a notification email for the certificate expiry reminders.
- Click Save at the top of the page.
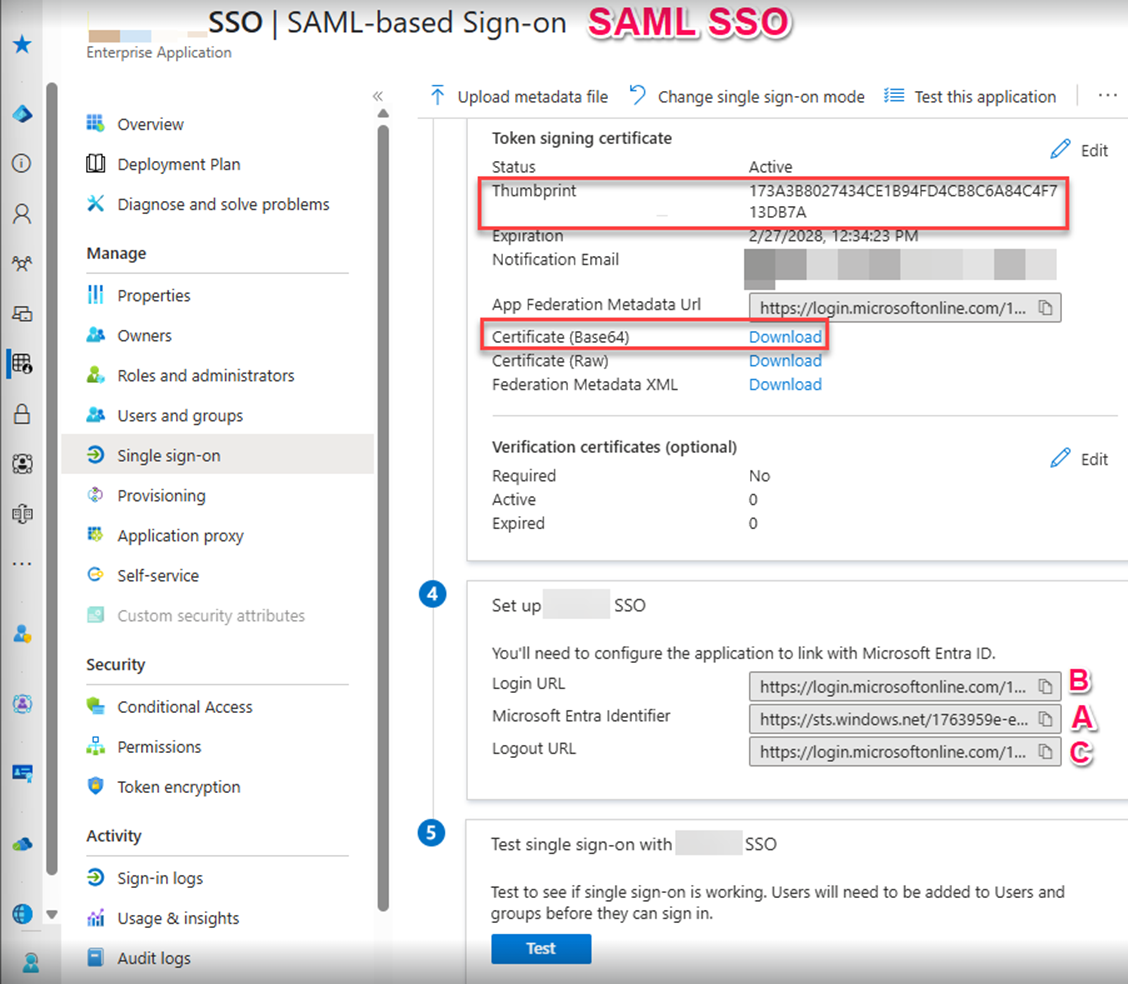
- Back on the setup page, next to Certificate (Base64), click Download to download the certificate file to the default download location on your device.
- Copy and securely store the Thumbprint.
Set up [Application Name]
In the Set up [Application Name] tile, copy and securely store the Login URL, Microsoft Entra identifier, and the Logout URL.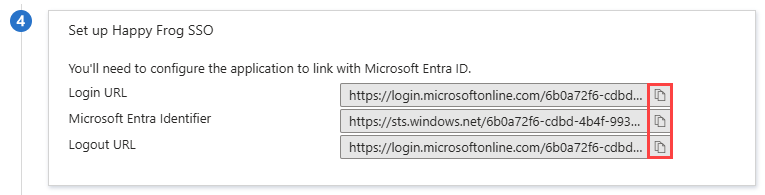
Test single sign-on with [Application Name]
- In the Test single sign-on with [Application Name] tile, click Test to check if single sign-on is working.
NOTE Leave the Azure portal open as you continue on to configuring IT Glue. You will need to refer to it frequently in the next section of this article.
Configuring SSO in IT Glue
Please make sure to follow the next steps to configure Basic SAML in Azure.
-
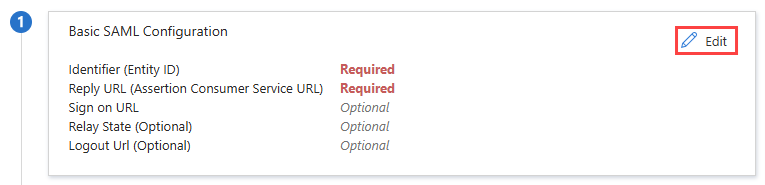
In the Basic SAML Configuration tile, click the Edit pencil icon.
-
Fill in the following fields, replacing [subdomain] with your own IT Glue subdomain:
-
Identifier (Entity ID):
-
Click Add identifier.
-
Enter your IT Glue subdomain (as it appears in [subdomain].itglue.com).
-
NOTE EU partners, please use [subdomain].eu.itglue.com. AU Partners, please use [subdomain].au.itglue.com.
-
Reply URL (Assertion Consumer Service URL):
-
Click Add reply URL.
-
Enter https://[subdomain].itglue.com/saml/consume.
-
-
Sign on URL: Enter https://subdomain.itglue.com
-
Relay State: This is an optional parameter used to tell the application where to redirect the user after authentication is completed, which you can leave blank.
-
Logout URL: Enter a URL to which IT Glue can redirect users after they log out of IT Glue.
NOTE IT Glue does not authenticate users into another application as IT Glue cannot act as an intermediary for SAML SSO between multiple website.
3. Click Save at the top of the pane when finished.
After completing the preceding configuration steps in Azure, you need to configure your IT Glue account to authenticate using SAML. You will need a few pieces of information from Azure to complete this step.
IMPORTANT It's highly recommended that before you begin the subsequent set of instructions, log in to your IT Glue account twice: once in a regular browser and once in an incognito/private window. Alternatively, you can also log in to two separate browsers. This is to ensure that you are still logged in to your account in case you are locked out in the other window.
- From the top navigation menu in IT Glue, click Admin.
- On the Settings page, click the Authentication tab.
- Turn on the Enable SAML SSO toggle. Once this is turned on, a form will appear. You will need to collect information from Azure and enter it into this form.
_with_Azure_pic02.png)
-
Copy the Microsoft Entra ID Identifier (a.k.a. SAML Entity ID) and paste it in the Issuer URL field.
-
Copy the Login URL (a.k.a. SAML Single Sign-On Service URL) and paste it in the SAML Login Endpoint URL field.
-
Copy the Logout URL (a.k.a. Sign-out URL) and paste it in the SAML Logout Endpoint URL field.
-
Go back to the previous page of the Azure settings and copy the Thumbprint and paste it in the Fingerprint field.
-
Open your Base64-encoded SAML Signing Certificate downloaded from Azure portal in Notepad, copy the content of it onto your clipboard, and then paste it in the Certificate field.
IMPORTANT Ensure there are no extra spaces trailing at the end of the Certificate string (i.e. after -----END CERTIFICATE-----).
To allow users to log in only with their SSO provider, enable Enable SSO Access Control option.
IMPORTANT Click Save only when all information has been entered. If you turn on SSO prematurely, it will break the login experience for all users on your account.
4. Click Save to complete the set up of your account.
Once you make this change, you can test your access.
Configuring SSO in MyGlue
Please make sure to follow the next steps to configure Basic SAML in your Azure.
If you are Setting up SSO for MyGlue, complete all steps as instructed in Configuring your MyGlue account for SSO. However, in step 2, you need to substitute different values as follows:
- Identifier (Entity ID): https://app.myglue.com (EU Partners use: https://app.eu.myglue.com) (AU Partners use: https://app.au.myglue.com)
- Reply URL (Assertion Consumer Service URL): https://app.myglue.com/saml/consume
- Sign on URL: https://app.myglue.com
- Logout URL: https://app.myglue.com/
When you reach the Configuring IT Glue section above, navigate instead to Account > MyGlue. In the Actions drop-down menu, select Edit. Then, scroll down to the Single Sign-on section and toggle the Enable SAML SSO switch to ON. Next, complete step 3 in that section but use the following values:

- Issuer URL -Microsoft Entra ID Identifier
- SAML Login Endpoint URL -Login URL
- SAML Logout Endpoint URL -Logout URL
NOTE For EU partners, please use https://app.eu.myglue.com. AU partners, please use https://app.au.myglue.com.
Now, you need to configure the MyGlue account to authenticate using SAML SSO. You will need a few pieces of information from your client’s identity provider to complete the steps.
-
In IT Glue, navigate to Account > MyGlue > Edit Account.
-
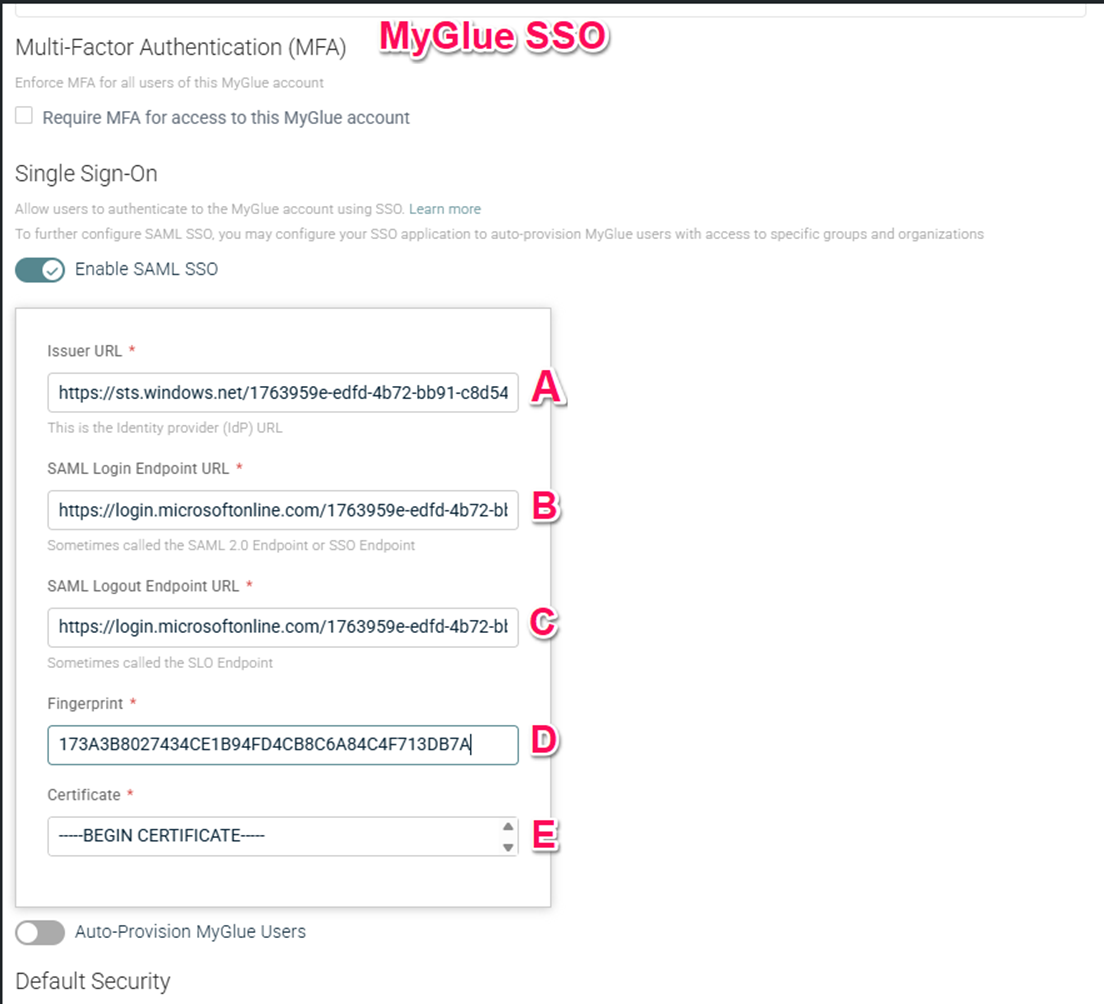
In the Single Sign-On section, turn the Enable SAML SSO toggle switch to ON. Once this is turned on, a form will appear. You will need to collect information from you client's identity provider and enter it into this form.
-
Issuer URL - The URL that uniquely identifies your SAML identity provider. Also called: Issuer, Identity Provider, Entity ID, IdP, IdP Metadata URL.
-
SAML Login Endpoint URL - The SAML login endpoint URL of the SAML server. IT Glue redirects to this URL for SSO if a session isn't already established. Also called: Sign-on URL, Remote login URL, SSO URL, SSO Endpoint, SAML 2.0 URL, Identity Provider Sign-in URL, IdP Login URL, Single Sign-On Service URL.
-
SAML Logout Endpoint URL - A URL where IT Glue can redirect users after they sign out of IT Glue. Also called: SLO Endpoint, SAML Logout URL, Trusted URL, Identity Provider Sign-out URL, Single Sign-Out Service URL.
NOTE IT Glue does not support SSO logout URLs.
-
Fingerprint - The appropriate value based on the information provided by your identity provider. Also called: Thumbprint.
-
Certificate - The authentication certificate issued by your identity provider (a base-64 encoded X.509 certificate). Be sure to include the entire certificate, including -----BEGIN CERTIFICATE----- and -----END CERTIFICATE------. Also called: Public Certificate, X.509 Certificate.
IMPORTANT Ensure there are no extra spaces trailing at the end of the Certificate string (i.e. after -----END CERTIFICATE-----).
IMPORTANT Click Save only when all information has been entered. If you turn on SSO before the information is entered, it will break the sign in experience for all users on your account.
-
Click Save.
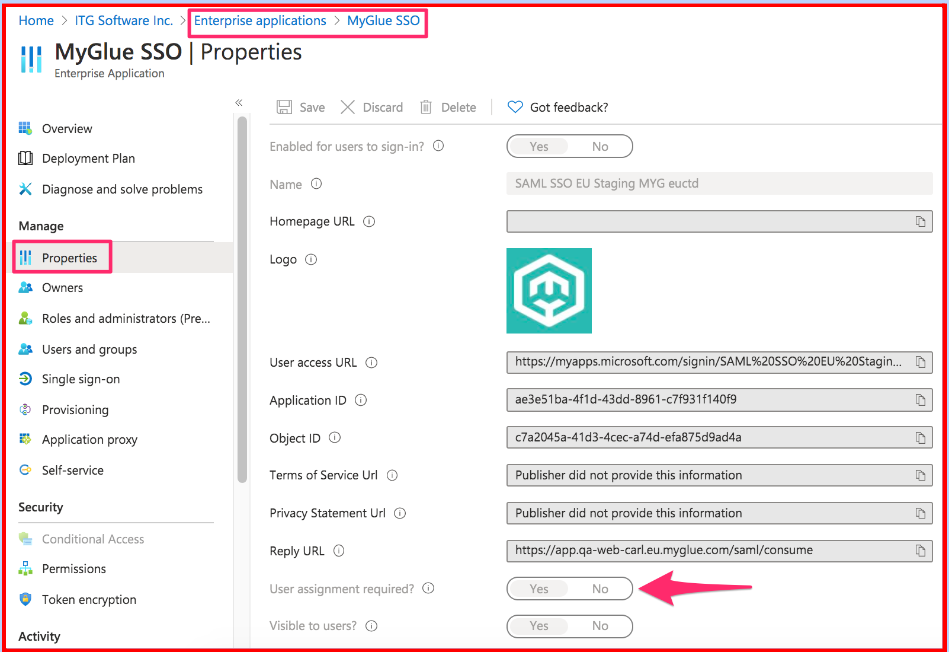
Finally, head back to the Azure portal and navigate to Microsoft Entra ID > Enterprise applications. Locate and open your newly created application in the list. In the left-hand menu, click Properties. Review the User assignment required toggle options:
- If you toggle the switch to YES, then users must first be assigned to this application before being able to access it. You will need to grant each new Azure user access to MyGlue.
- If you toggle the switch to NO, then any users who navigate to the application deep-link URL or application URL directly will be granted access. All new Azure users created will automatically have access to MyGlue.
Testing SSO authentication
In the above section, you should have created two IT Glue browser sessions. If you are locked out, you will be able to use the incognito/private window to turn off SSO while you investigate the cause.
To make sure SSO is working, perform these steps:
- Log out of and close the Azure management portal and the Microsoft Entra ID access panel.
- In a new browser session, navigate directly to the access panel at myapps.microsoft.com.
- Enter your Microsoft Entra ID credentials to log in. After authentication, you will be able to interact with the applications integrated with the directory.
- Click on the SSO application you created to be redirected and logged in to IT Glue.
Another way to test SSO access is to go to your account subdomain ([subdomain].itglue.com) directly.
SSO FAQ
When the SSO server is unavailable, how do we access our accounts?
If your SSO provider's service is unavailable, you can still log in to IT Glue via app.itglue.com using your username and password.
If your SSO is not working, confirm your provider's service is available and submit a Kaseya Helpdesk request for assistance.
How do we disable SSO for a user?
An IT Glue Administrator or Manager can disable a user account from the Users page. Refer to Adding and removing users. Disabling user accounts through the SSO server is not currently supported.