BitLocker Recovery Keys
BitLocker recovery keys from Intune devices stored in the Microsoft Intune admin center (intune.microsoft.com) will be automatically documented and kept up to date in IT Glue. You can access your BitLocker recovery keys from Intune devices associated with IT Glue configurations in organizations. By accessing it, you can view each BitLocker recovery key as a general password. BitLocker recovery keys auto documentation feature is available only if you have purchased Network Glue.
NOTE All Network Glue users with access to the organization can access BitLocker recovery keys as passwords.
Prerequisites
-
Must to have an active Microsoft Integration setup.
-
The BitLockerKey.Read.ALL API permission must be added on the Microsoft side when configuring a Microsoft integration. Type should be Delegated.
-
Select at least one type of licenses, contacts with which you would like to sync under IT Glue > Microsoft Integration > Sync Settings > Contacts.
-
The checkbox for BitLocker Sync Settings under IT Glue > Microsoft Integration > Sync Settings must be enabled.
NOTE Only Network Glue administrator or Manager can access BitLocker Sync Settings in IT Glue.
-
The checkbox for Sync Intune Devices under IT Glue > Microsoft Integration > Sync Settings > Intune tab must be enabled.
-
Devices stored in Microsoft must be matched with IT Glue configurations under IT Glue > Microsoft Integration > Matching.
Procedure
-
To gain access to BitLocker recovery keys in IT Glue, you need to select at least one type of licenses, contacts with which you would like to sync and enable the option Sync BitLocker Recovery Keys under Microsoft Entra ID Sync in the Microsoft Integration sync settings page.
NOTE This option is visible to all users irrespective of whether they have purchased Network Glue or not.
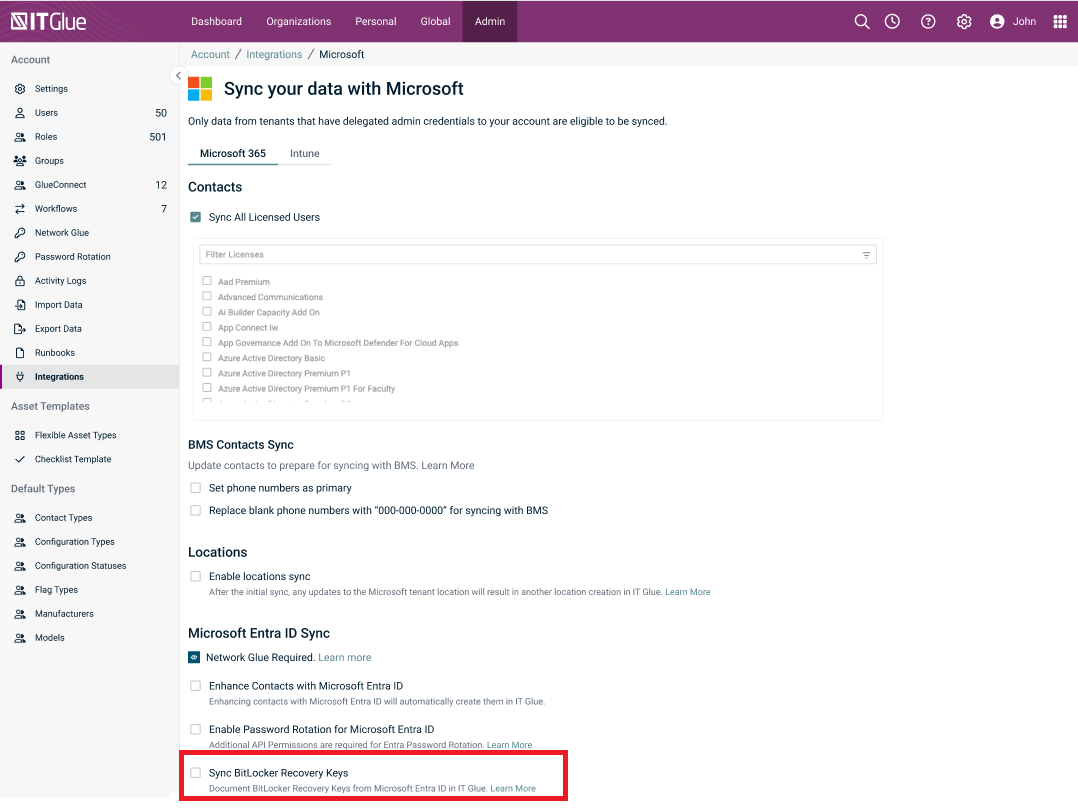
IMPORTANT If you already have an existing Microsoft Integration, the sync setting for BitLocker will be disabled by default. In such a scenario, you first need to add BitLockerKey.Read.ALL API permission in Microsoft integration from the Microsoft’s website. Only then, will you be able to enable the BitLocker sync setting in IT Glue.
If you do not have a Microsoft integration, the sync setting for BitLocker will be enabled by default. In this scenario, you first need to go to Microsoft’s website and configure the Microsoft integration from scratch. Ensure that you have added BitLockerKey.Read.ALL API permission. Then create a Microsoft Integration in IT Glue. -
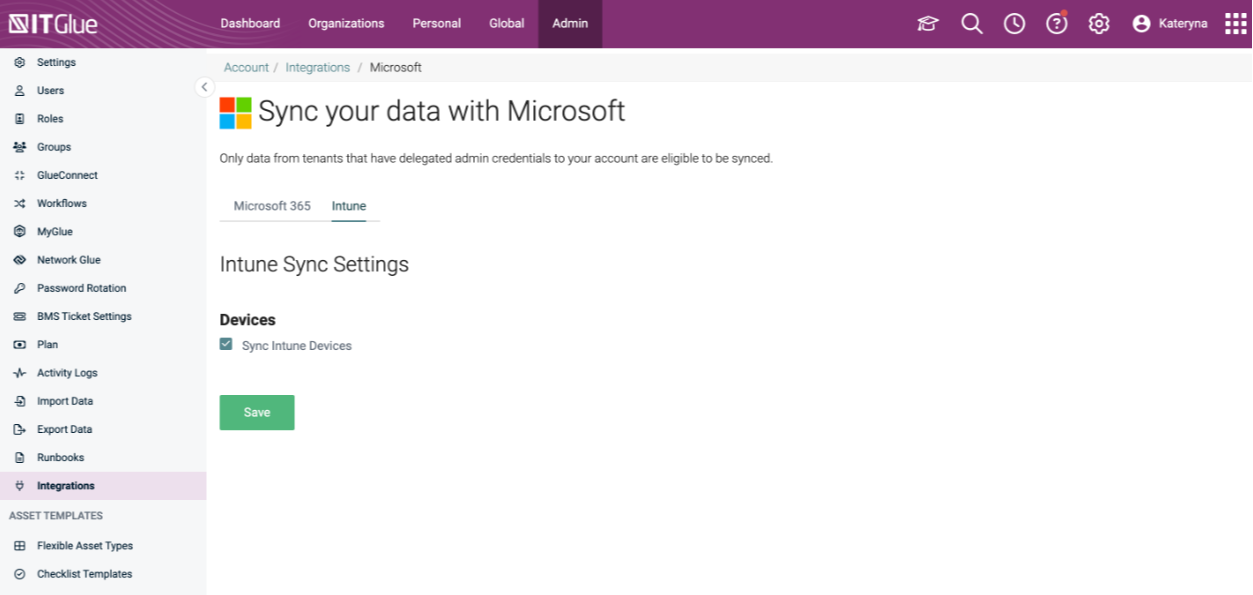
Ensure that the checkbox for Sync Intune Devices is enabled under IT Glue > Microsoft Integration > Sync Settings > Intune tab.
-
Match devices stored in Microsoft Intune with IT Glue configurations under IT Glue > Microsoft Integration > Matching.
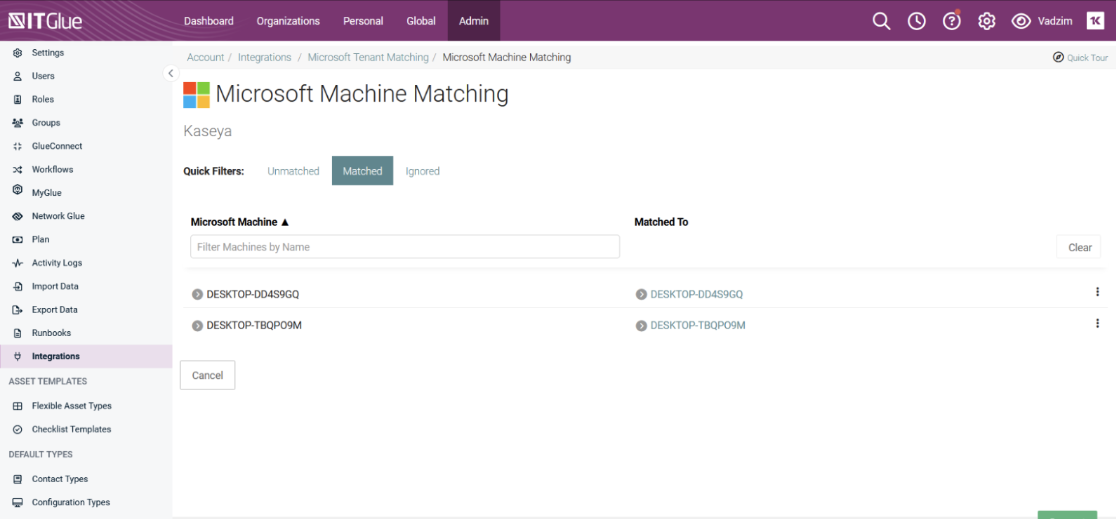
After a successful sync with Microsoft, users who have purchased Network Glue will be able to see the BitLocker Keys (via Network Glue) folder and the Bitlocker Recovery keys as passwords on the Password List view page.
Viewing passwords created in BitLocker recovery keys
-
Navigate to the organization to which the password belongs to.
-
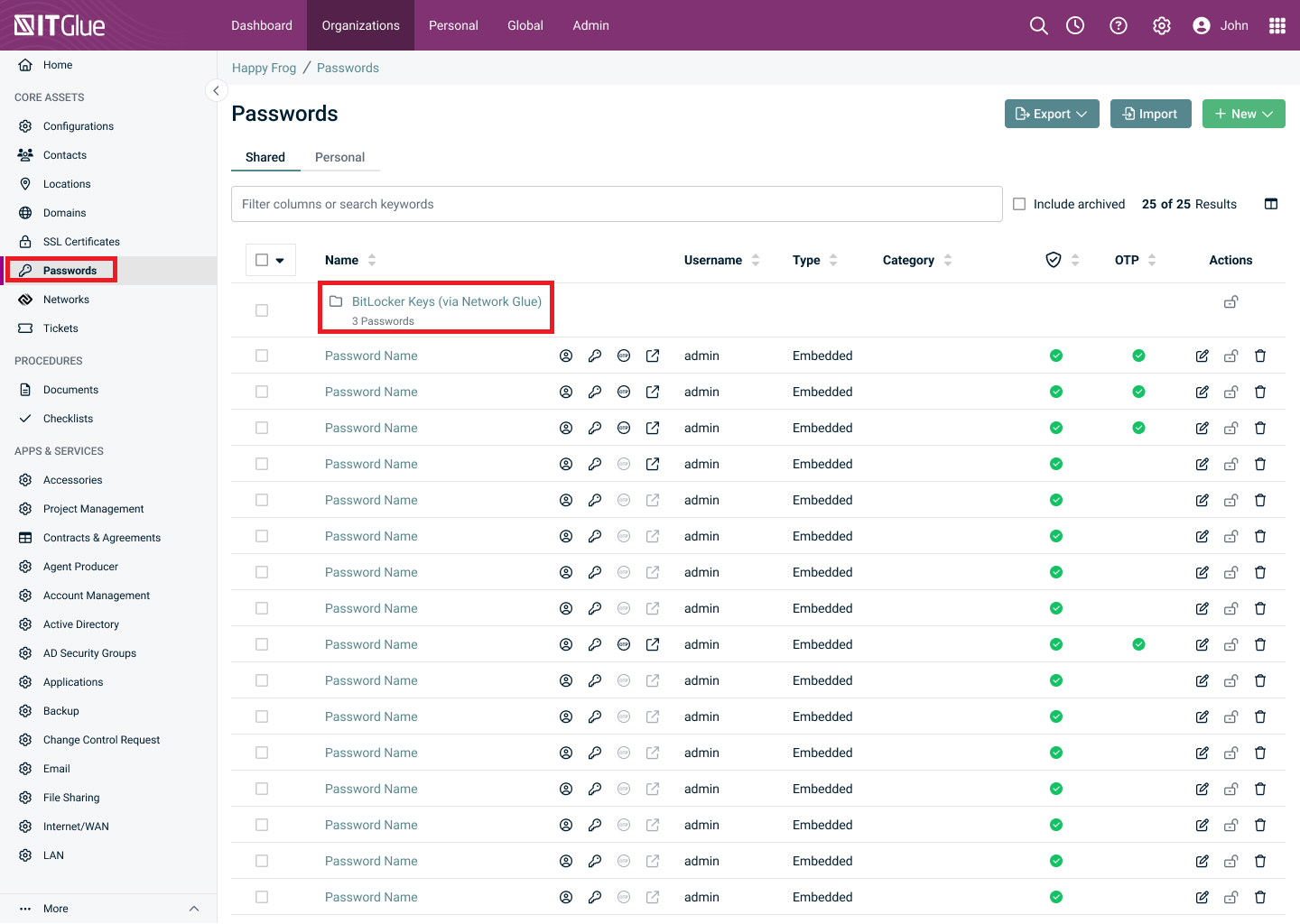
Click on Passwords in the left sidebar.
-
Click on the BitLocker Keys (via Network Glue) folder.
-
View the list of BitLocker Recovery Keys and click on the one for which you wish to view the password record.
Filter down BitLocker recovery keys by the BitLocker Keys (via Network Glue) category.NOTE You will not be allowed to create a category with the same name category as “BitLocker Keys (via Network Glue)“.
-
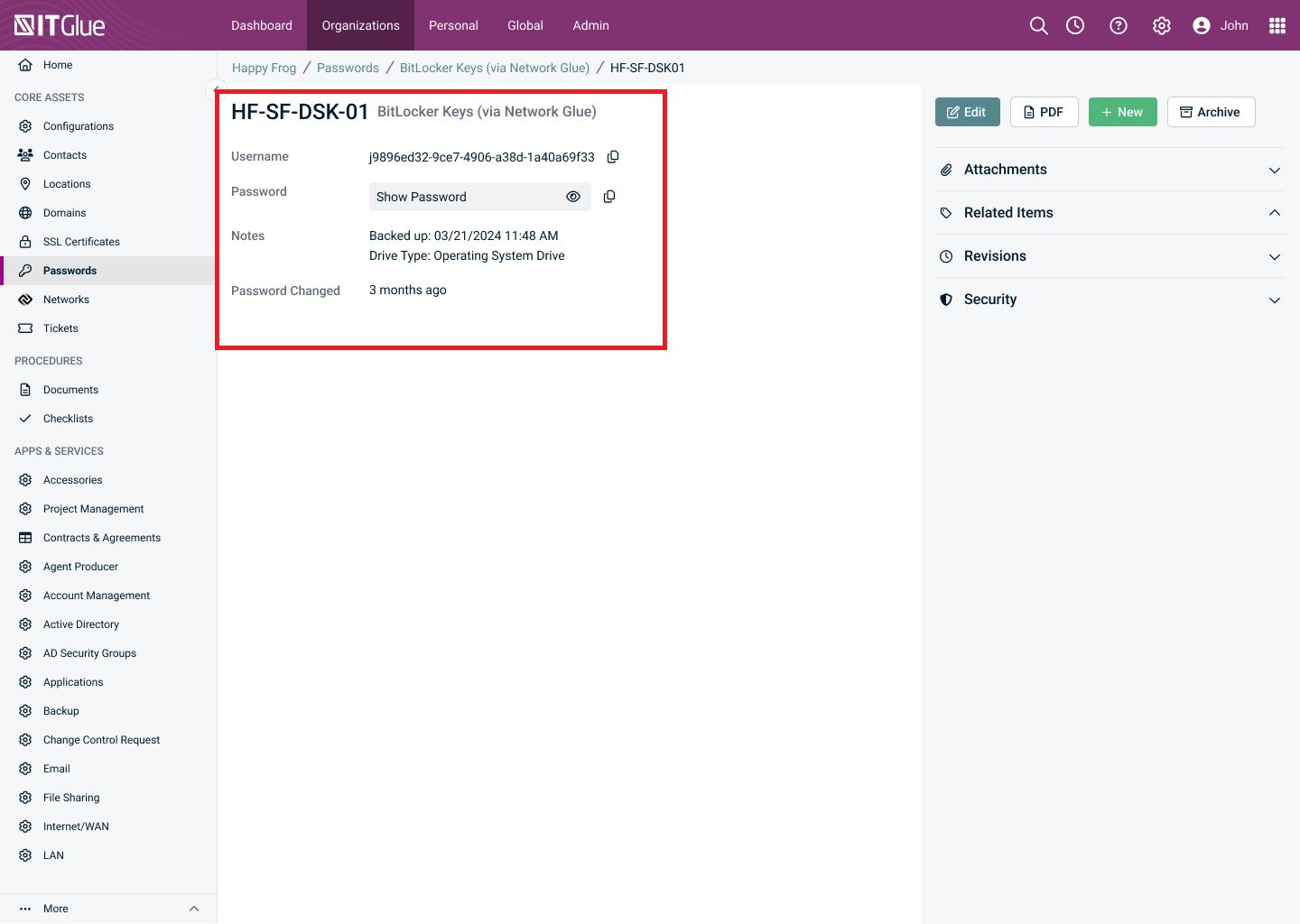
View the BitLocker recovery key as a password record.
-
The name of the password displayed corresponds to the device name stored in Microsoft Intune.
-
Username is the BitLocker recovery key ID.
-
The Password value is the BitLocker recovery key collected from Microsoft Intune.
-
Notes:
-
IT Glue users are not allowed to name a folder in IT Glue using this exact word as in "BitLocker Keys (via Network Glue)". While this folder can be moved if within the same organization but cannot be moved to other organizations.
-
The latest BitLocker recovery key is visible in the BitLocker keys (via Network Glue) folder. To view previous keys, enable the Include archived checkbox settings.
-
An IT Glue user is not allowed to edit or delete "BitLocker Keys (via Network Glue)" folder. This is done to prevent a user from unintentionally editing the folder where the BitLocker Keys pulled from Microsoft are stored.
-
When an IT Glue admin has not created a configuration in IT Glue, the BitLocker Recovery Keys will not be created as general passwords as there will be nothing to match using Intune devices. An admin needs to create a configuration in IT Glue first. Once it is created, devices can be matched from Intune to the configurations in IT Glue and BitLocker Recovery Keys can be created as general passwords.
NOTE BitLocker recovery keys saved as general passwords are not allowed for password rotation.
-
"BitLocker Keys (via Network Glue)" will be hidden if an IT Glue admin loses Network Glue subscription or has not purchased it.
-
An IT Glue admin cannot add their own items in the "BitLocker Keys (via Network Glue)", as when they do not update Network Glue subscription, all their personal information will be lost.
-
You are not allowed to move BitLocker recovery keys stored as general passwords outside of the folder.
-
Only up-to-date keys will are visible. All outdated BitLocker recovery keys will be automatically archived. However, you can unarchive archived BitLocker recovery keys, if needed.
-
You can store BitLocker recovery keys in Vault.
-
You are not allowed to delete BitLocker recovery keys as general passwords.
Edit Password page
You cannot edit the Name, Category, Username, Password and Notes in the Edit Password page. This information is automatically pulled from Microsoft and cannot be changed in IT Glue.
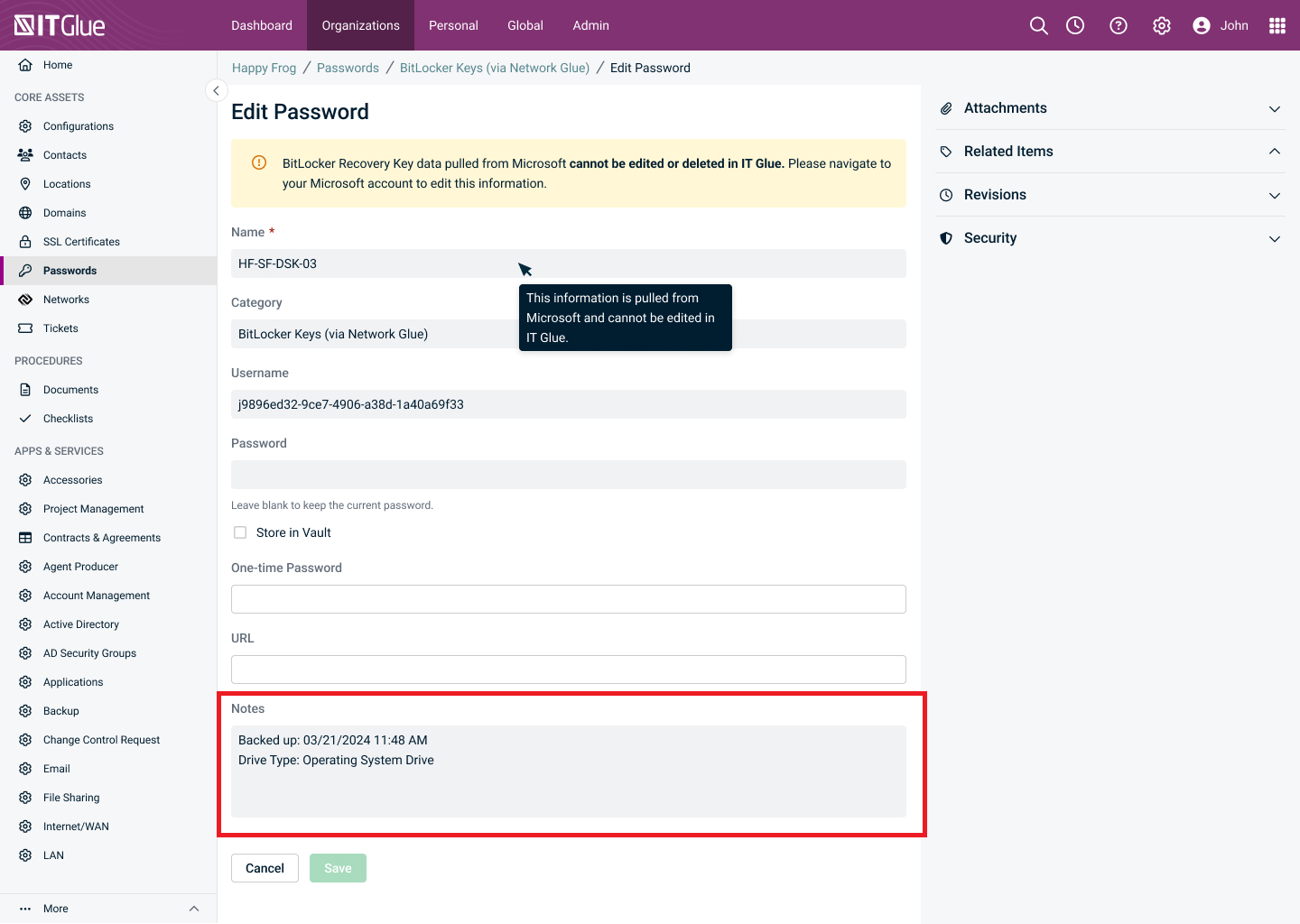
NOTE If changes are required, you need to make necessary changes in Microsoft. After a successful sync, all changes performed in Microsoft will be visible in IT Glue.
BitLocker recovery key as a password
BitLocker recovery key as a password is related to the IT Glue configuration to which it is associated with.
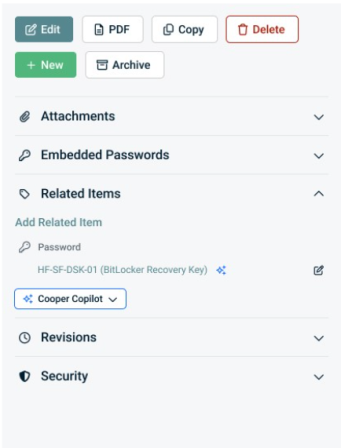
When BitLocker recovery key as a password is created, archived, accessed and viewed, it will be recorded as an action in activity logs.



